Installing RADIUS-Bridge on a Linux Endpoint
Introduction
RADIUS (Remote Authentication Dial-In User Service) is a protocol that provides centralized authentication, authorization, and accounting (AAA) for users who connect to a network. RADIUS is widely used in various network access technologies, including wireless networks, VPNs, and dial-up services. The protocol enables network administrators to manage access policies and ensure that only authorized users can access network resources. RADIUS operates by securely passing authentication data between the client, the RADIUS server, and the network access device, often using a shared secret for encryption.
Overview
This guide provides detailed instructions for installing and configuring RADIUS-Bridge on a Linux endpoint. Follow these steps carefully to ensure a successful setup.
Prerequisites
- Linux Machine: Ubuntu/Debian recommended
- Access: Root/sudo privileges required
- Network Connectivity: Stable internet connection needed
- Port 1812: Must be available for RADIUS authentication
Installation Process
1. Initial Setup
- Access the AuthNull Dashboard
- Navigate to the Endpoint Page
- Go to RADIUS section
- Select RADIUS under Add Radius Device
4. Installation Verification
Check the FreeRADIUS service status:
# Check service status
sudo systemctl status freeradius
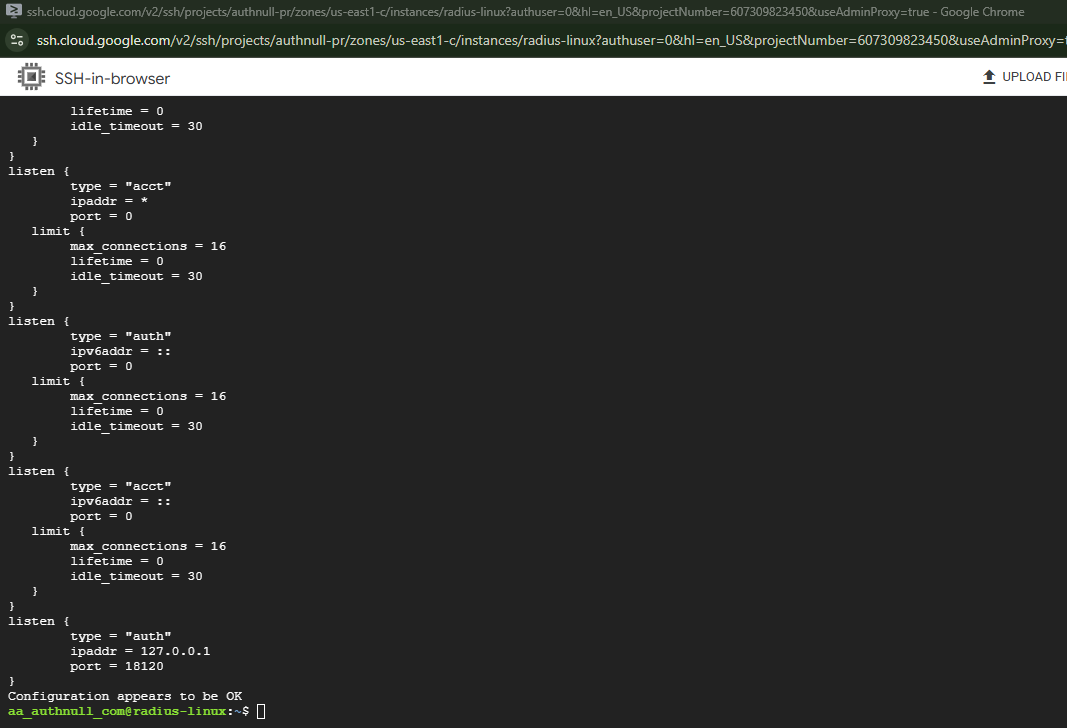
Verify configuration in debug mode:
# Run in debug mode
sudo freeradius -XC
5. Local User Testing
i. Add a test user by editing the users file:
# Edit users configuration file sudo nano /etc/freeradius/3.0/users
ii. Add the following configuration:
username ClearText-Password := "password"
Reply-Message := "Hello, %{User-Name}"
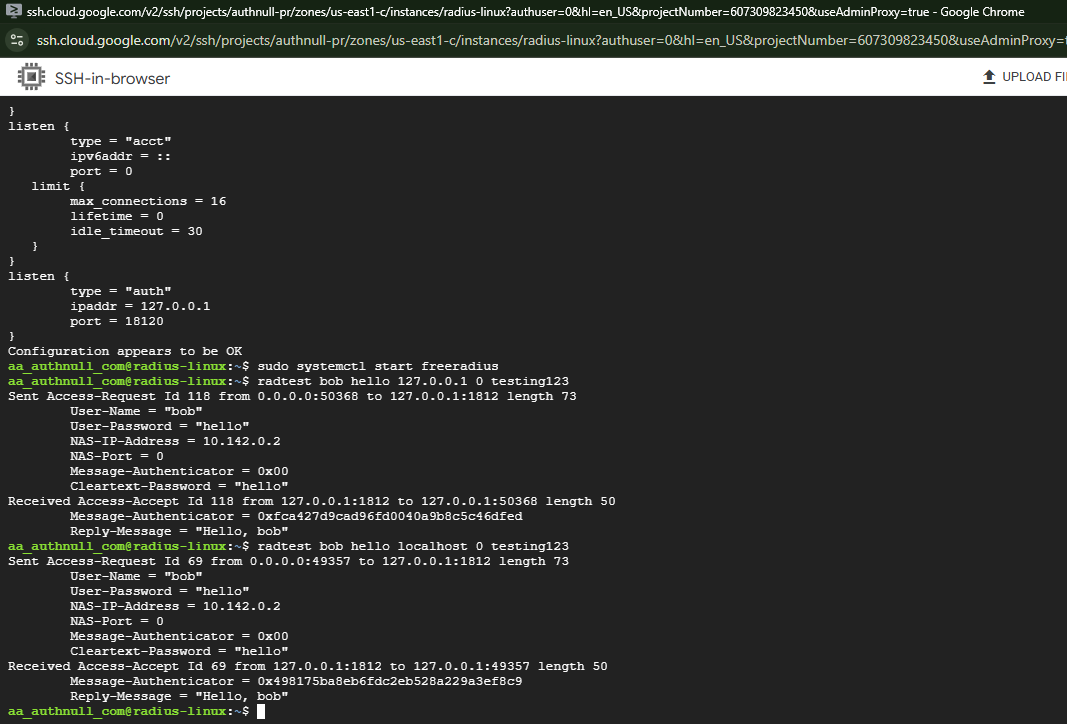
iii. Test authentication:
# Test local authentication radtest username password 127.0.0.1 0 testing123
RADIUS Module Configuration
1. Configure RADIUS Client
Edit the clients configuration file:
# Edit RADIUS client configuration
sudo nano /etc/freeradius/3.0/clients.conf
Add this configuration block:
client name {
ipaddr = <IP-ADDRESS>
secret = <SHARED-SECRET>
require_message_authenticator = no
}
Verification and Monitoring
Verify Configuration and Permissions:
- Check Module Exists:
ls -l /etc/freeradius/3.0/mods-enabled/authnull_2fa - Check binary exists and is executable:
ls -l /usr/local/bin/authnull_2fa - Check FreeRADIUS configuration:
sudo freeradius -XC - Verify Fluent Bit is installed and running:
sudo systemctl status fluent-bitsudo journalctl -u fluent-bit - Check logs:
tail -f /var/log/freeradius/radius.logtail -f /var/log/radius_2fa.logSecurity Best Practices
Shared Secret Management
- Store securely
- Rotate regularly
- Use strong encryption
Access Control Measures
- Limit server access
- Monitor logs regularly
- Keep software updated
Network Security
- Configure firewall rules
- Use secure protocols
- Conduct regular security audits
Troubleshooting Guide
Service Issues
If the service won’t start, verify:
- Port availability
- Configuration syntax
- System resources
- Service logs
Authentication Problems
If authentication fails, check:
- Shared secret configuration
- NPS settings
- Network connectivity
- Log files for errors
Connection Problems
Troubleshooting steps:
- Verify network connectivity
- Check port accessibility
- Test local authentication
- Review firewall configuration